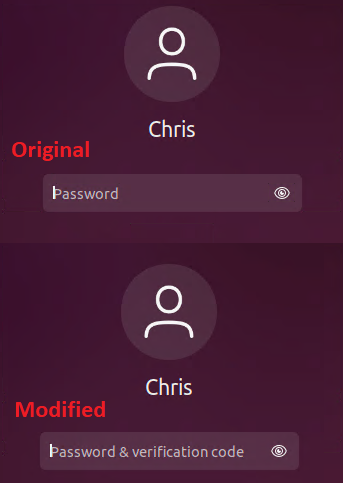
How to Setup 2FA in Ubuntu Using Google Authenticator

I wanted to add 2 Factor Authentication (2FA) to my local Ubuntu virtual machine using Google Authenticator. None of the writeups I found online covered all of my use cases, so I pieced together a solution that did. This is how I set it up…
sudo apt install libpam-google-authenticator
google-authenticator
Upon running the google-authenticator command, you will be shown a URL, a QR code, a secret key, and a prompt for you to enter the 6-digit code from your authenticator app.

Take note of (aka: WRITE IT DOWN and stash it somewhere secure) the secret key, verification code, and emergency scratch codes because if you lose your authenticator app, you’ll be locked out unless you have these to get back in/re-do your 2FA setup.
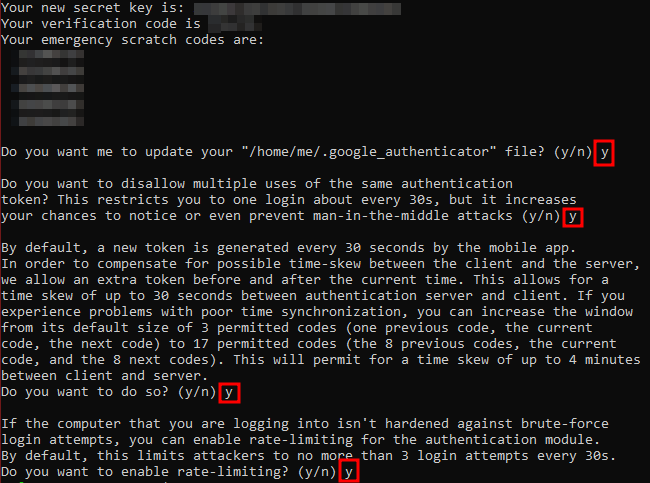
Once you’ve answered the prompts you’ll have a .google-authenticator file in your home directory.
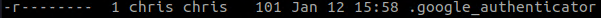
This file contains your secret key/emergency scratch codes as well as settings/values for the prompts we just answered.
Okay, now that we’ve done that, we need to tell Linux to actually use this form of authentication.
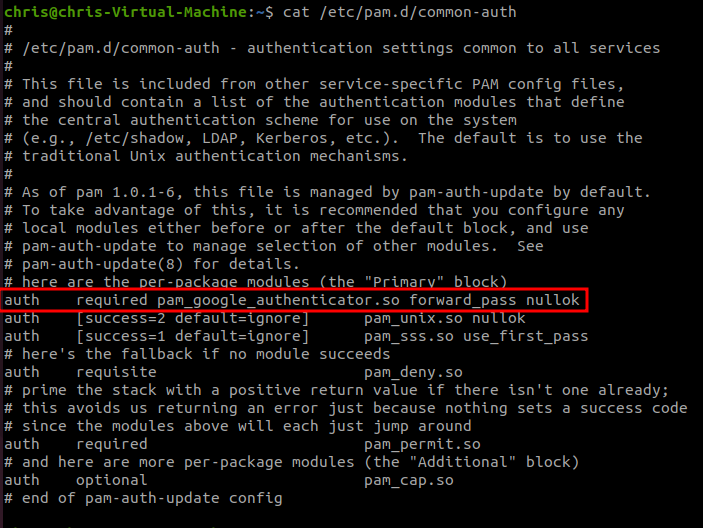
sudo nano common-auth
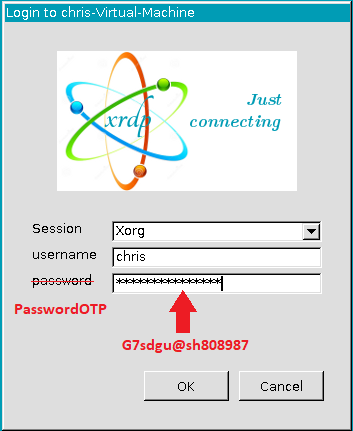
For common-auth, we need to add auth required pam_google_authenticator.so forward_pass nullok somewhere (immediately?) above the pam_unix.so module. This will ensure that we get prompted for our password+2FA first. This will take care of local console login as well as sudo.
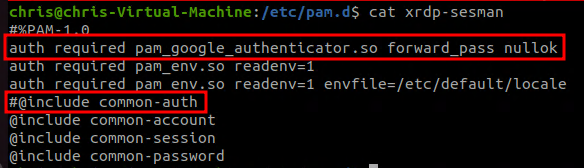
sudo nano xrdp-sesman
For xrdp-sesman, we need to add the same line auth required pam_google_authenticator.so forward_pass nullok and comment out the “common-auth” line.
Give yourself a reboot and you’ll be in business.