Securing our home/office network

Our home network started off like most. We had a cable modem and a wireless router - two little boxy things plugged into the wall. We had internet; everything worked.
Fast forward a few years - We now have a public-facing web server hosting several sites (I jokingly refer to this as “Bob’s Bargain Basement Hosting”), a whole bunch of PC’s/laptops/phones/IoT devices, a Plex server, security cameras, WiFi out the wazoo, and occasionally nefarious people poking around looking for a way in.
Our simple network had grown to a hodgepodge of switches, routers, and Wifi repeaters, all connected via rats nest of cat6. Oh, and everything was running on a single subnet. It’s a matter of time before one of our public-facing sites gets popped and evildoers are routing around in my network. Or just as likely (if not more so) - they already have. Time to shore up this mess.

Our aging Netgear GS105 started randomly shutting off ports.
The Plan
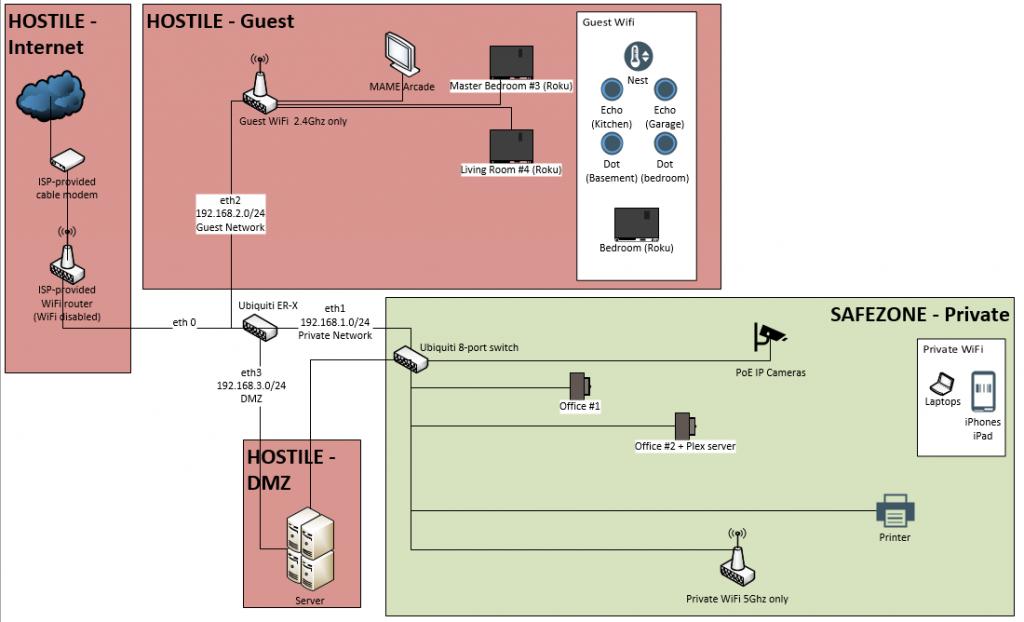
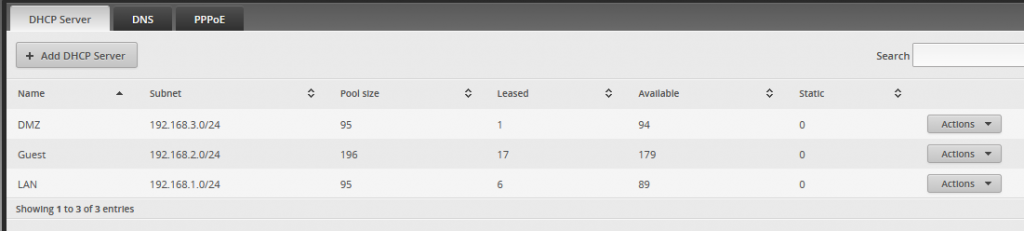
I decided to have 3 subnets:
192.168.1.0/24 is the private network - PC’s we trust, our phones, printer, etc.
192.168.2.0/24 is the guest network - IoT devices, TV-streaming devices, etc.
192.168.3.0/24 is the DMZ network - Public-facing websites, sketchy VMs, etc.
Every nerd has a napkin drawing, post-it note scribble, or Visio diagram of their network, right?
The Ubiquiti EdgeRouter-X is where all the magic happens. It has 5 ports, and I’ve given each port a job. Eth0 is where the internet comes in. Eth1 is for the .1 (Private) segment, eth2 is for the .2 (Guest) segment, and eth3 gets the .3 (DMZ) segment. Eth4 is unused; keep reading and you’ll find out why.
When messing with subnets/firewall rules it becomes very easy to lock yourself out of the router. I know, because I’m an idiot and did this exact thing. The only way back in is to hard-reset the router.
Thankfully, I had been using the Ubiquiti Network Management System (UNMS) which automatically takes configuration backups.
For those unfamiliar, Ubiquiti’s UNMS is a graphical configuration/management tool for their EdgeMAX line of equipment. It’s available in SaaS form on their website, but they also have a Docker container in case you want to run it locally. Similarly, they also have a UniFi controller which performs a similar function, but is for their UniFi series of equipment. It’s a bit annoying that they aren’t all tied together, but that’s another post for another day…
Once I hard-reset the router back to the defaults, I was able to restore a backup config (from before my subnet changes), and everything was back to normal. I’m so thankful for this because redoing all the firewall rules and re-configuring the OpenVPN server would’ve taken me several hours.
Always have a plan B
I suppose UNMS was my plan B, but what if I didn’t have that in place? That’s where the last port, eth4, comes into play. That port is assigned an IP address in its own range (10.10.1.1) and isn’t the subject to any firewall rules. If I do something dumb and lock myself out I can always assign my laptop a static IP of 10.10.1.2, plug into that port and access the router.
Having 3 subnets means I also have 3 DNS servers
Before I jump into the firewall rules, it helps to know what our goals are.
- Minimize internet exposure. Port 443 for the web server, and one additional port for OpenVPN.
- Assume that the web servers will get breached. Limit the amount of damage an attacker can do.
- The guest network shall be treated as hostile. Rokus, Amazon Echos, crappy imported IoT devices, questionable virtual machines, or a skid with a cantenna pointed at our house…I trust none of them. This network just needs internet access and nothing else.
- The private network is wide open. I trust (but verify) anything on this network. One notable exception are the security cameras which I’ve written about in the past.
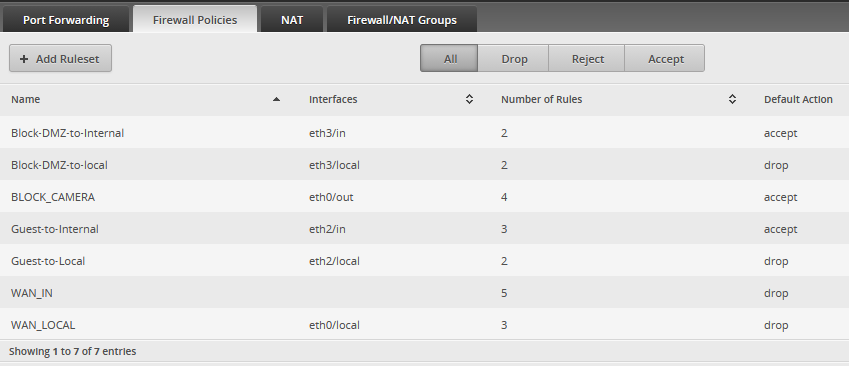
Firewall Rules
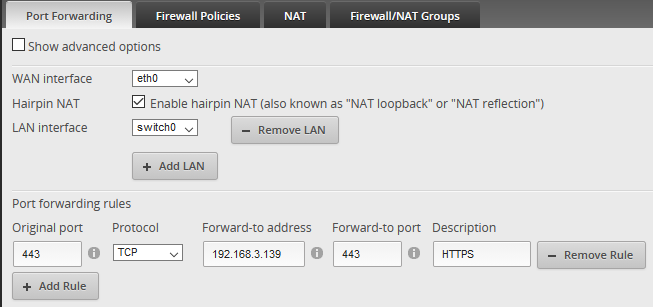
Port-forwarding HTTPS traffic to our web server.
We have port-forwarding enabled for HTTPS traffic to hit our web server. In fact, it’s technically hitting a reverse proxy server. Since I have plenty of CPU/storage/RAM to work with, I spun up dedicated web servers behind the proxy for isolation. Remember when I said “assume breach”? If one of my sites gets popped, the attacker will only have access to that dedicated server. He/She will still have to work damn hard to move laterally.
10,000 ft view of the Firewall Policies
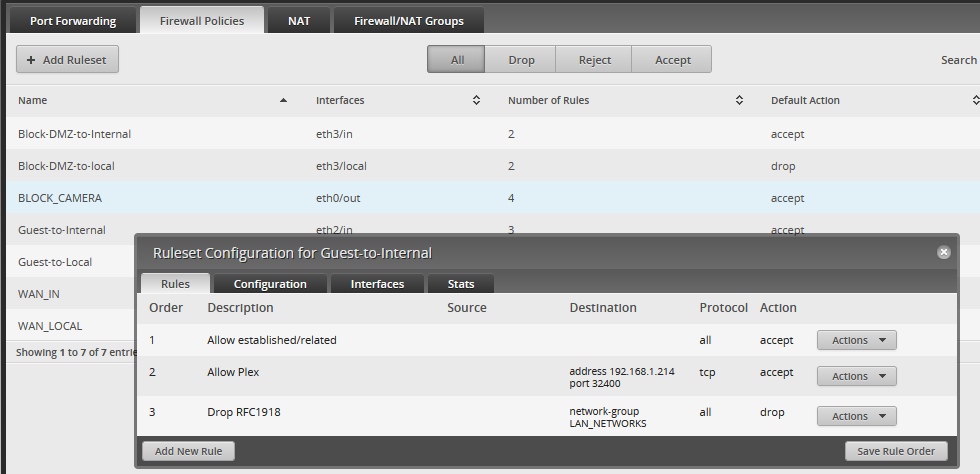
DMZ and Guest Firewall Rules
I lump these two together since they’re almost identical.
These are the Guest Rules
We have one pinhole open to our private network specifically for port 32400 - that lets all our guest network’s devices access Plex, which is on the private network (for now). We drop all packets destined for LAN_NETWORKS, which I’ve defined under “Firewall/NAT Groups” as any internal IP range (192.168.0.0/16, 172.16.0.0/24, and 10.0.0.0/8). The rest of the traffic, destined for the internet, is allowed. The DMZ network is setup the same minus the Plex pinhole.
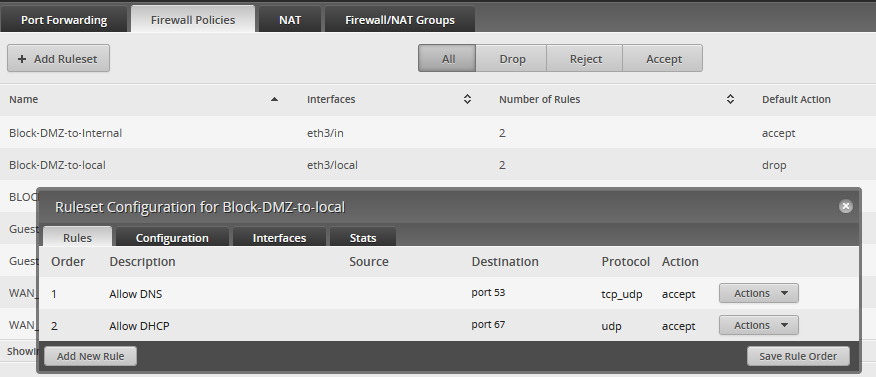
These are the rules setup for router access
DMZ and Guest networks’ access to the router is restricted in that we, by default, drop all traffic. The only allowable traffic to the router itself is for DNS and DHCP. Realistically, I could trim this back since our DMZ machines’ IP addresses are all statically assigned, and I could probably get rid of DNS as well. The Guest network has the same set of rules. For that network, I definitely want/need DNS and DHCP services running.
I don’t have a screenshot of it, but our WAN-to-Local rules are setup to drop all traffic by default and accept OpenVPN traffic.
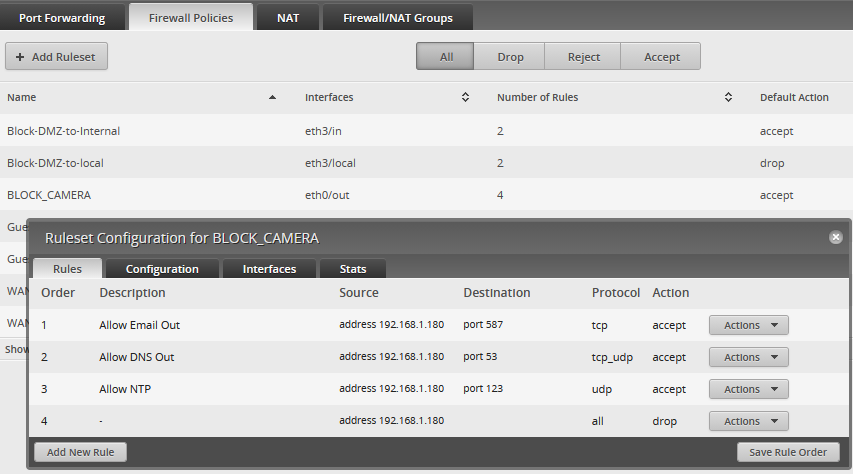
Security cameras (specifically, the network video recorder) are locked down
I allow DNS, Network Time Protocol, and SMTP over TLS. That’s it. Everything else gets dropped. I’ll eventually move this to the guest network once I replace our Guest network’s WiFi with one that supports guest isolation. That’s our biggest gap at the moment.
After organizing our firewall rules, it was time to organize some of the wiring :)
That’s a wrap! Hopefully this sparks some ideas on how to make your network more secure.